If you are not using a password manager, what are you doing with your life?!
I’ve been using VaultWarden or Bitwarden for a couple of years now. I even made a video about it that will be linked below.
Bitwarden Security Issues
Last month Flashpoint found a vulnerability in Bitwarden that was covered on Forbes:
Newly published research from threat intelligence experts, Flashpoint, has suggested that Bitwarden falls short in one particular area: the auto-filling of credentials within embedded iframes. What the vulnerability researchers at Flashpoint found was that the Bitwarden browser extension could auto-fill the login credentials field if they were found to be saved within the Bitwarden password vault. So far, so absolutely normal.
This made me think about looking into a new password manager and recently I’ve been seeing different creators making content about a password manager called Passbolt.
Just a quick interjection to remind you that, if you find my content interesting and/or would like to help support the channel, you can do the easiest thing in the world and click the subscribe button down below. If you’d like to support in other ways, you can become a channel member, join my Patreon, or get access to my content without ads for as little as $1/month over at dbtech.fans.
Requests for Passbolt
I’ve also had a few different people ask me to make a video about Passbolt so I spent some time looking into it and, overall, Passbolt LOOKS great!
I really thought I was going to like Passbolt as a self-hosted password management solution. But we’ll get more into that in a bit.
After digging around on the site and whatnot, I spent a few minutes going through the setup process and it was surprisingly easy to get set up in Docker. It was just as easy as deploying a docker-compose, attaching a URL to it and getting started.
The simplicity of getting it set up was actually really nice. And there are some great videos out there about getting it set up in Docker, so be sure to check those out!
After playing with it off and on for a month, I’ve got some thoughts that I want to share with you about why I can’t recommend Passbolt for the average self-hoster or home-labber.
I just want to be clear:
I’m not saying Passbolt is a bad product. I just think that it’s not a great option for people who are hosting a password manager for their friends and family.
Let me explain.
Users Can See TOO Much For No Reason
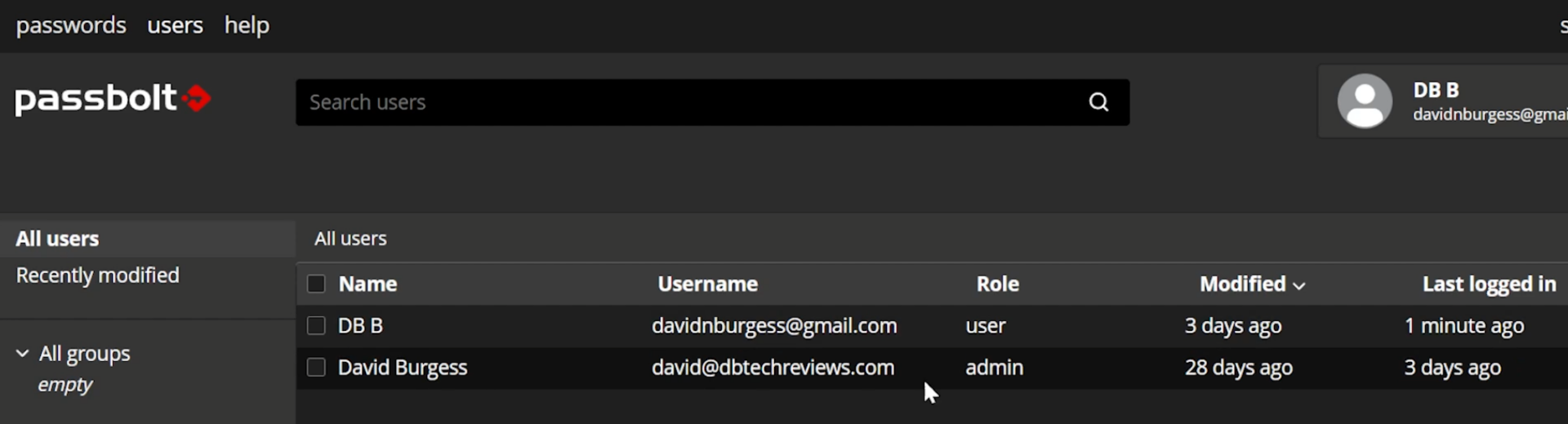
First, All users can see all other users on the site. This isn’t something that has just gone unnoticed and has flown under the radar. This is something that I was able to find forum posts going back to 2018 where people wanted the ability to turn this off.
Resource Link: https://community.passbolt.com/t/as-an-admin-i-do-not-want-my-users-to-see-all-users-on-the-platform/1151
More than just being able to just see other user accounts, all users can see when all other users were last logged in and when they last updated something in their password vault.
WHAT? WHY?
The forum post says: “This is to enable sharing entries. People need to be able to see their details and public key for verification.”
WHAT? I’ve used several other password managers in the past and this was never brought up. If I wanted to share a password with someone, I just put in their email address and shared it. I didn’t pick from a list of other users on the server.
Browser Extension REQUIRED
You HAVE to have their browser extension installed to use the web app. If you don’t have the extension installed in your browser you can’t access your vault.
There’s an FAQ about this topic, but basically, it’s the extension that renders the login page.
Also, the extension stores your authentication data and handles authentication locally and then logs you in via an API rather than actually sending your password over the internet to the server for authentication.
While I can see why they might want to add this for security, this isn’t super user-friendly for the average user.
Resource Link: https://help.passbolt.com/faq/discover/why-an-extension
Signing Out and Back In
If you sign out of your account and go to sign back in, you have to go through a password recovery process that requires a PGP file that downloads to your system when you first create your account. Even if you KNOW your password and just want to log into your account on a new browser (with the extension installed), you have to have your PGP file in order to authenticate yourself and login via the API.
Changing your Password
The passphrase is stored on your device and never sent server side. Changing your passphrase will only change it locally. If you have multiple browsers configured, the passphrase will need to be changed in all places individually.
So… if you change your password on one device, it only applies to THAT device and not all of your other logged-in accounts.
A Decent Mobile Experience
The mobile experience is a bit more user-friendly and you can have multiple accounts on your device and you don’t need to fuss with a PGP key to get logged in.
All you have to do is:
- Install the app on your phone
- Login via the web interface
- Go to the Mobile Setup link in your profile
- Click the Start button
- Scan the Dynamic QR code on the web page with the Passbolt app and you’re set.
You can also add a fingerprint authentication to get access to your passwords faster when you’re on the go
You can do this with as many of your accounts as you’d like and then toggle between them by just tapping your fingerprint.
2 Factor Authentication
Additional security can be added via 2 Factor Authentication.
There are 3 different types of 2FA available:
- Time-based one-time passwords
- Yubikey
- Duo
I’ve only used the Yubikey method, but I can say that it’s super simple to implement as an admin.
Get a Yubico API Key
- Head over to https://upgrade.yubico.com/getapikey/
- Enter your email address
- Plug in your compatible Yubikey and touch the gold pad on it. this will fill in the information about your Yubikey
- Click submit and then you’ll get a Client Identifier and a Secret key
- Head back over to your Passbolt instance and login as an admin
- Then go over to the “administration” tab and then toggle “Yubikey” to the “on” position
- Enter the Client Identifier and the Secret key in the appropriate boxesClick Save at the top of the screen
Now your individual users can set up 2FA with their own Yubikey devices.
Emails Galore!
You’ll need to have an email server available for setup so you can get the information you need to get password recovery emails and that sort of thing.
Something to be aware of, though, is the default email settings. By default ALL of the available email notification settings are set to “ON” which means every time you change anything or login or whatever, there’s a good chance that an email will be sent. Also, when you add a new entry to your password vault, you’ll get an email.
When I exported my password list from VaultWarden and imported it to Passbolt, I received HUNDREDS of emails; one for EACH password that was added.
The thing is that, as a user, there’s nothing you can do about this. Only an admin can turn notifications off and that’s a global setting and there don’t appear to be any user-specific changes available.
Other Notes about Passbolt
There is an option to turn off self-registration if you don’t want just any Tom, Dick, and Harry to be able to set up an account on your server.
There are a few different themes to choose from.
So Who Is Passbolt for?
I think it’s easier for me to tell you who Passbolt isn’t for:Passbolt isn’t for users who will be easily frustrated by technologyPassbolt isn’t a password manager for your friends and family
I don’t think this is the password manager for the masses. I think they’ve got a target demographic and have built their application with that in mind. They didn’t build Passbolt for home-labbers and self-hosters.
Passbolt is, as it says on their website: for organizations that take their security and privacy seriously, including Fortune 500 companies, the defense industry, universities, startups and many others.
If you’re still interested in getting passbolt set up for your own use, there are some great videos out there about getting it set up in Docker, so be sure to check those out!
I also want to thank Yubico for sending over their Experience Pack of their newest generation of 2FA keys for me to take a look at. I’ll have links to those in the description down below

